IP Protection in the Fashion and Apparel Industry (Part 2)
.
By Richard Stobbe
As noted in Part 1, IP rights in the fashion and apparel industry are fiercely contested. Fashion products can be protected in Canada using a number of different IP tools, including:
- confidential information
- patents
- industrial design or “design patentâ€
- trademarks
- trade dress
- copyright
- personality rights.
For many products, there will be an overlap in protection, and we’ll discuss some examples. In Part 2, let’s review the next couple of areas:
- Industrial Design or “Design Patentâ€:
I always tell my clients not to underestimate this lesser-known area of IP protection. It can be a very powerful tool in the IP toolbox. In both Canada (which uses the term industrial design) and the US (which refers to a design patent), this category of intellectual property only provides protection for ornamental aspects of the design of a product as long as they are not purely functional . To put this another way, features that are dictated solely by a utilitarian function of the article are ineligible for protection.
Registration is required and protection expires after 10 years. A registrable industrial design has to meet certain criteria: (i) it must differ substantially from the prior art (in other words it must be “originalâ€); (ii) it cannot closely resemble any other registered industrial designs; and (iii) it cannot have been published more than a year before application for registration. Some examples: 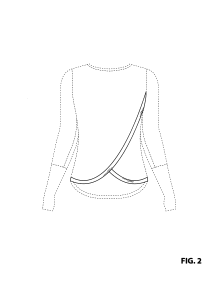 This depicts a recent registration by Lululemon. The design comprises the pattern feature of a shirt as depicted in solid lines in the drawings. (The portions shown in stippled lines do not form part of the design.)
This depicts a recent registration by Lululemon. The design comprises the pattern feature of a shirt as depicted in solid lines in the drawings. (The portions shown in stippled lines do not form part of the design.)
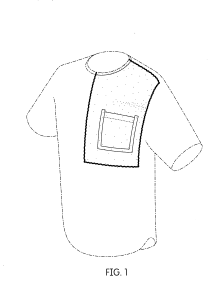
The solid lines on the image above represents a protected design registration filed by Nike.
TIP: Placement of a pocket on a t-shirt may not be considered innovative, but even minor differentiators can help distinguish a product in a crowded field. A design registration can support a blended strategy which also deploys other IP protection, such as trademark rights.
- Trademarks:
Every consumer will be intuitively familiar with the power of a brand name such as LULULEMON or NIKE, or the well-known Nike Swoosh Design. That topic is well-covered elsewhere. However, some brands take advantage of a lesser-known area of trademark rights: distinguishing guise protects the shape of the product or its packaging. It differs from industrial design, and one way to consider the distinction is that an industrial design protects new ornamental features of a product from when it is first used, whereas a distinguishing guise can be registered once it has been used in Canada so long that becomes a brand, distinctive of a manufacturer due to extensive use of the mark in the marketplace. It’s worth noting that the in-coming amendments to the Trademarks Act will do away with distinguishing guises.
One good example is the well-known shape of CROCS-brand sandals. The shape and appearance of the footwear itself has been used so long that it now functions as a brand to distinguish CROCS from other sandals. Just as with industrial design, the protected features cannot be dictated primarily by a utilitarian function.
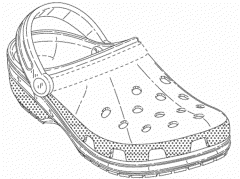
Others have filed distinguishing guise registrations in Canada, including Canada Goose Inc. for coats and Hermès International for handbags.
TIP: For a distinguishing guise application, each applicant will have to file evidence to show that the mark is distinctive in the marketplace in Canada. That is not the case with a regular trademark, such a word mark or regular logo design.
We review the final areas of IP protection in Part 3.
Calgary – 7:00 MST
No comments
Protective Order for Source Code
By Richard Stobbe
A developer’s source code is considered the secret recipe of the software world – the digital equivalent of the famed Coca-Cola recipe. In Google Inc. v. Mutual, 2016 BCSC 1169 (CanLII),  a software developer sought a protective order over source code that was sought in the course of U.S. litigation. First, a bit of background.
This was really part of a broader U.S. patent infringement lawsuit (VideoShare LLC v. Google Inc. and YouTube LLC) between a couple of small-time players in the online video business: YouTube, Google, Vimeo, and VideoShare. In its U.S. complaint, VideoShare alleged that Google, YouTube and Vimeo infringed two of its patents regarding the sharing of streaming videos. Google denied infringement.
One of the defences mounted by Google was that the VideoShare invention was not patentable due to “prior art†– an invention that predated the VideoShare patent filing date.  This “prior art” took the form of an earlier video system, known as the POPcast system.  Mr. Mutual, a B.C. resident, was the developer behind POPcast. To verify whether the POPcast software supported Google’s defence, the parties in the U.S. litigation had to come on a fishing trip to B.C. to compel Mr. Mutual to find and disclose his POPcast source code. The technical term for this is “letters rogatory” which are issued to a Canadian court for the purpose of assisting with U.S. litigation.
Mr. Mutual found the source code in his archives, and sought a protective order to protect the “never-public back end Source Code filesâ€, the disclosure of which would “breach my trade secret rights”.
The B.C. court agreed that the source code should be made available for inspection under the terms of the protective order, which included the following controls. If you are seeking a protective order of this kind, this serves as a useful checklist of reasonable safeguards to consider.
Useful Checklist of Safeguards
- The Source Code shall initially only be made available for inspection and not produced except in accordance with the order;
- The Source Code is to be kept in a secure location at a location chosen by the producing party at its sole discretion;
- There are notice provisions regarding the inspection of the Source Code on the secure computer;
- The producing party is to test the computer and its tools before each scheduled inspection;
- The receiving party, or its counsel or expert, may take notes with respect to the Source Code but may not copy it;
- The receiving party may designate a reasonable number of pages to be produced by the producing party;
- Onerous restrictions on the use of any Source Code which is produced;
- The requirement that certain individuals, including experts and representatives of the parties viewing the Source Code, sign a confidentiality agreement in a form annexed to the order.
A Delaware court has since ruled that VideoShare’s two patents are invalid because they claim patent-ineligible subject matter.
Calgary – 10:00 MST
No commentsNon-Disclosure & Confidentiality: A Cautionary Tale
.
By Richard Stobbe
A confidentiality agreement is signed. So… confidentiality is covered, right?
This 2014 case, nClosures Inc. v. Block and Company, Inc., No.13-3906 & 14-1097 (7th Cir., Oct. 22, 2014), shows that the answer is “not so fast”. In the nClosures case, two companies entered into a confidentiality agreement to explore a potential business deal to manufacture iPad cases based on nClosures’ so-called “Rhino” and “Rhino Elite” designs. However, the first confidentiality agreement was specifically directed to the purpose of initial discussions exploring the possibility of a deal. nClosures disclosed its confidential Rhino and Rhino Elite designs to Block.
However, in the following months, the parties circulated a draft manufacturing agreement but did not ultimately sign any written agreement, nor did they address confidentiality obligations that extended beyond those initial discussions. Eventually, the parties settled on a vague verbal arrangement to manufacture and sell iPad cases.
In this decision, the U.S. Seventh Circuit Court of Appeals provides us an important reminder. For confidentiality to apply, that first agreement is important, but remember:
1. As the business relationship expands beyond those initial discussions, additional confidentiality obligations should be imposed, to cover the new expanded purposes;
2. A non-disclosure or confidentiality agreement is not effective if the disclosing party does not make reasonable efforts to preserve confidentiality over its confidential information. In this case, the court found that nClosures had disclosed the same confidential design information to other contractors and designers without any confidentiality obligations.
In the words of the Court: “…no additional confidentiality agreements were required of individuals who accessed the design files for the Rhino or Rhino Elite devices. Additionally, neither the Rhino nor the Rhino Elite drawings were marked with words such as ‘confidential’ or ‘contains proprietary information’. Furthermore, the drawings were not kept under lock and key, nor were they stored on a computer with limited access.”
Lessons for business? A confidentiality agreement is an important first step, but it must be followed up with additional confidentiality agreements as the relationship evolves, and it must be backed-up with internal policies of proper marking, restricted access, and lock-and-key protections, in order to preserve confidentiality.
Calgary – 07:00 MT
No commentsCourt of Appeal Upholds Injunction Against Google (Equustek Solutions Inc. v. Google Inc.)
.
By Richard Stobbe
Apparently Google does not appreciate being ordered by a Canadian court to remove worldwide search results. In Update on Injunction Against Google (Equustek Solutions Inc. v. Google Inc.) we reviewed a 2014 decision in which Google was ordered to de-index certain offending websites which were selling goods that were the subject of an intellectual property (IP) infringement claim (that decision was Equustek Solutions Inc. v. Jack, 2014 BCSC 1063 (CanLII)). Google appealed that decision to the B.C. Court of Appeal.
Last week, in Equustek Solutions Inc. v. Google Inc., 2015 BCCA 265, the B.C. Court of Appeal upheld the original order.
In the underlying action, Equustek alleged that Mr. Jack and Datalink Technologies designed and sold product which infringed the IP rights of Equustek. The original lawsuit was based on trademark infringement and misappropriation of trade secrets. Equustek successfully obtained injunctions prohibiting this original infringement. The infringement, however, continued through a variety of websites, and relying on search engines (such as Google) to attract customers. Equustek obtained another injunction prohibiting Google (“the world’s most popular search engine” – those are the court’s words) from delivering search results which directed customers to the offending websites.
Google appealed, arguing that this injunction was overreaching since it was beyond the Canadian court’s jurisdiction. After all, Google has no employees, business offices, or servers within British Columbia. The appeal court observed that Google’s “activities in gathering data through web crawling software, in distributing targeted advertising to users in British Columbia, and in selling advertising to British Columbia businesses are sufficient to uphold the chambers judge’s finding that it does business in the Province.” The court, therefore, was entitled to assert jurisdiction over Google even though it was not a party to the underlying litigation. Put another way, “the underlying litigation clearly has a “real and substantial connection†to British Columbia. Equally, Google’s services, which provide a link between the defendant’s products and potential customers, are substantially connected to the substance of the lawsuit.”
The court drew a parallel with a recent English case, Cartier International AG v. British Sky Broadcasting Limited, [2014] EWHC 3354 (Ch.), where Cartier sought an injunction against a number of ISPs in the UK in order to block access to the offending websites which sold counterfeit Cartier products. The court granted the order in that case.
The B.C. court rejected a creative free-speech argument (the argument that the injunction may have the effect of stifling freedom of expression from the blocked websites). (“There is no evidence that the websites in question have ever been used for lawful purposes, nor is there any reason to believe that the domain names are in any way uniquely suitable for any sort of expression other than the marketing of the illegal product.”)
The court also gave short shrift to the argument that the injunction should be restricted to “Canadian” results from google.ca as opposed to an injunction with worldwide effect (“…an order limited to the google.ca search site would not be effective.”)
If Google successfully appeals this decision, it will undoubtedly attract even more intervenors and will provide an opportunity for Canada’s top court to clarify the law in this area.
Need assistance with intellectual property disputes and internet law? Get advice from experienced counsel.
Calgary – 07:00 MDT
No commentsCompeting After Employment (Part 2)
.
By Richard Stobbe
A few weeks ago, Jawbone, a fitness tracking hardware and software maker, sued its arch-rival Fitbit, alleging that Fitbit lured its employees away to obtain access Jawbone’s confidential information and product plans. How would this play out in Canada? In our earlier post (Competing After Employment (Part 1)) we considered a case in which the employer could not describe the confidential information with enough specificity and detail, and the employer was unable to get its injunction form the court.
In Brandt Engineering Products Ltd v Rockford Engineering Works Ltd., 2014 SKQB 339 (CanLII), the employer enjoyed a different result.
After several employees left BEPL to join a competitor, BEPL sued its competitor alleging that the former employees of BEPL each breached their fiduciary duties, breached confidence, and breached their employment contracts, among other things. BEPL sought an injunction to prevent the use of confidential information by the ex-employees and their new employer.
The court noted that “each of these individuals were either professionals or they were engaged in doing, assisting or supporting the work of the professional/design team at BEPL. I am satisfied from the evidence that each of them would have been aware of the confidential and proprietary nature of the designs, processes, customer and supplier lists and generally and specifically financial, organizational and technical information respecting BEPL and its operations. Whether by virtue of their employment contracts, their status as professionals, the confidentiality and proprietary notices which much of BEPL’s documentation contained, or the role that each of the individual defendants played as members of the design group at BEPL, each could not help but be aware of and recognize the confidential and proprietary nature and character of much of the information to which they had access and were privy.” (Emphasis added)
It was discovered during the course of the lawsuit that the ex-employees had downloaded or removed various confidential documents (“approximately 9,713 documents” burned onto discs and a “banker’s box of BEPL materials”) and provided some of this information to the new employer, BEPL’s competitor.
The court granted the injunction restricting the ex-employees and their new employer from using confidential information and upholding the non-solicitation covenants. The court made a few important points which bear repeating:
1. “Where employees have a non-competition clause in their contract of employment or they are determined to be employees having fiduciary obligations – the employee has a continuing duty to maintain confidences for a reasonable period of time and the employee is not permitted to actively solicit the former employer’s customers nor to use confidential information to the employee’s own employment advantage…”
2. “An interim injunction should not issue for the sole purpose of eliminating competition or effectively reducing it. In cases such as this, the purpose of the injunction is to constrain improper competition — that is to say the use or potential use by former employees of confidential and proprietary information, the property of and acquired from a previous employer to whom the employees owe a fiduciary duty of confidentiality, to compete with that employer.”
3. It is also worth noting that:
– the terms of the employment agreements as well as internal confidentiality notices helped bolster the argument that these ex-employees were aware of their confidentiality obligations, and
– the evidence of misappropriation of specific documents avoided the problem in the JTT Electronics case regarding the need to describe the confidential information with enough specificity and detail.
In summary, this case succeeded in enjoining improper competition by departing employees. Get advice on departing employees, restrictive covenants and intellectual property protection from experienced counsel.
Calgary – 07:00 MDT
No commentsReverse Engineering Cloud-Based Software
.
By Richard Stobbe
Let’s say you provide web-based software in a SaaS subscription model. What if your reseller or strategic business partner works against you to redesign and reverse engineer your software so they can launch a competing product?
This is what happened to Warehouse Solutions (WSI) in the recent U.S. case Warehouse Solutions, Inc. v. Integrated Logistics, LLC (May 8, 2015, Fed. CA 11th Cir.). WSI developed and sold a web-based software product known as “Intelligent Audit” which interfaced with UPS and FedEx tracking systems to allow companies to track and manage packages. Integrated acted as a reseller of “Intelligent Audit”, but was also a competitor to WSI, in the sense that Integrated sold its own package-tracking software. The reseller relationship between WSI and Integrated, however, was never documented in a written agreement. The parties had verbal discussions about the confidential and proprietary nature of the “Intelligent Audit” software.
Although Integrated never had access to the source code for “Intelligent Audit”, it had high level administrator access rights to the software, and therefore had much broader insight into the features, functionality and structure of the software, compared to the typical end-user.
On the side, unknown to WSI, Integrated developed its own web-based package-tracking software product that was visually and functionally similar to “Intelligent Audit”. Integrated even went so far as to give its own software developer access to “Intelligent Audit”. Eventually, Integrated dropped “Intelligent Audit” and began selling its own competing product under the ShipLink brand name.
WSI then sued Integrated for reverse engineering and copying its software, and through various court proceedings, the claims came down to the issue of trade secrets. The court drew a distinction between a software program’s underlying source code, which may be a trade secret, and the program’s “look and feel†and “functionality,†which cannot be protected as a trade secret, since these features are readily apparent to any user. Since WSI did not enter into a written confidentiality agreement with Integrated, the trade secret claim failed, and WSI’s claim was dismissed.
Lessons for business?
1. It’s worth noting that this case turns largely on U.S. concepts of “trade secret” protection under the Trade Secrets Act, and there is no equivalent legislation in Canada. Canadian software vendors are frequently bound by local U.S. laws in their dealings with American customers, resellers and strategic partners, so this case is an important one for Canadian SaaS providers, even though it involves U.S. law.
2. There are situations – such as in AirWatch, LLC v. Mobile Iron, Inc., (Unpublished) No. 1:12-cv-3571 (N.D. Ga. Sept. 4, 2013) – where a software licensor can protect its software as a trade secret, where it uses written agreements to clearly preserve the secrecy of the program’s functions and specifications.
3. Overall, the message for software vendors and SaaS providers is that clear written agreements will always be preferable to handshake deals and verbal warnings about confidentiality.
Calgary – 07:00 MDT
No commentsCompeting After Employment (Part 1)
-Â
By Richard Stobbe
A key employee departs. The employer, worried that confidential information has leaked out of the company, scrambles to respond. After a frenzied period of preparation, the employer starts a lawsuit and seeks an injunction against the ex-employee.
In these two recent Canadian cases, those same basic facts apply but with very different results. First, let’s look at the BC case decided in December 2014 (JTT Electronics Ltd. v. Farmer, 2014 BCSC 2413). In that case, the employer sued the ex-employee and the employee countered with an argument that the employer could not actually identify the confidential info it sought to protect.
The Court agreed, noting: “The need to identify with some reasonable degree of specificity what a plaintiff asserts is confidential or proprietary serves three important and related functions.” To summarize:
- It enables the ex-employee to respond to the lawsuit, and to bring into question whether the purported confidential information is actually confidential or whether it is information that is in the public domain.
- If the employer can establish that specific information in its possession is confidential, and the remaining elements of an injunction are made out, the ex-employee can understand (by virtue of the court order) what it is that he or she can or cannot do.
- Unless there is a “reasonable level of precision or definition”, it is difficult or impossible for the court to enforce the order.
Because the employer could not describe the confidential information with enough specificity and detail, the order was not granted.
Next, the non-solicitation and non-competition clauses which purportedly bound the ex-employee were, by the court’s analysis, “undefined”, “ambiguous”, “overly broad”, since they appeared to impose a worldwide ban which imposed a “blanket prohibition of unlimited geographic scope on any post-employment competition” by the ex-employee. On that basis, the Court refused to grant an order to enforce these restrictive covenants.Â
Lessons for business?
- “Confidential information” is broadly understood to be “anything that is valuable because it is secret to the company.” But in the case of an injunction application, courts will require a clear, specific definition of what exactly constitutes confidential information in this case, as it relates to this company and this ex-employee. While the definition in the underlying agreement – for example, a confidentiality agreement, non-disclosure agreement, employment agreement or even a shareholders agreement – is likely to remain broad, the specificity must come into play at the point where the court order is sought.
- Ensure that non-competition restrictions are carefully drafted, are reasonable in their scope, and consistently use defined terms. For example, in this case, the defined term “Business” was given a particular meaning in one section, but the seemingly generic term “business” was used in another section. This caused the court to question why the two terms would be different, and merely added to the court’s finding of ambiguity.
Â
Calgary – 07:00 MST
No commentsIntellectual Asset Management Best Practices – Part 2
 –
In Part 1, we looked at three important steps in starting an intellectual asset management process within your organization. “Intellectual assets†can include the know-how and intellectual capital within your organization together with registered and unregistered intellectual property (IP), inventions, trade-secrets, patents, copyright-protected works, trademarks, industrial designs, and other forms of IP.
As we reviewed in Part 1, intellectual asset management starts with (i) an internal IP audit, coupled with (ii) internal education about the strategic importance of intellectual property within the organization; and (iii) the organization should establish a screening process, to weigh the various factors that influence how to innovate through “make versus buy†decisions.
In Part 2, we take a deeper dive. An organization can be innovative without being commercially successful. In other words, there is often a gap between the creative process of innovating, and the successful commercialization of those innovations. By implementing the steps in Part 1, an organization becomes more sophisticated in its treatment and analysis of intellectual assets, and an organization will develop a culture in which IP is understood and valued. That helps close that gap. However, this does not necessarily mean that intellectual assets will become an engine of economic value. That requires the development of additional skills and competencies within the organization. Consider the following “next stepsâ€:
- Strategic Alignment: Let’s be clear. IP should not drive the organization. Rather, the strategic goals of the organization should inform the intellectual asset management strategy. Ensure that IP policies are aligned with the strategic goals of the organization. Consider the organization in question: is this a university? A government research lab? A medium-sized for-profit business, or maybe it’s a growing business with markets in multiple jurisdictions.
- How is success measured for this organization?
- Are there immediate goals of raising capital?
- Entering a new international market?
- Attracting investors?
- Making a strategic alliance or partnership?
- Should the IP policy reflect a defensive or offensive position?
All of these organizations will have different strategic goals and must ensure that their intellectual asset management strategy reflects and supports the overarching goals of the organization. IP is only one piece of the puzzle.
- Gap Analysis: An IP audit is focussed primarily on taking an inventory of the organization’s intellectual assets. A ‘gap analysis’ is the next step: it’s an assessment of what’s missing from the organization’s IP toolbox. What does the organization need in order to achieve its goals? And how can the gaps in the organization’s IP inventory be filled, considering the strategic goals involved. This internal analysis can lead to an external, “outward looking†review. What is available in the marketplace, either through acquisition, in-licensing or strategic partnership? See also the “make versus buy decisions†discussed in Part 1. In connection with the analysis of “gaps†in the IP portfolio, look at any gaps in the paper: How do employment agreements and consultant agreements deal with IP ownership issues and confidentiality? Do vendor or supplier agreements need to be bolstered to address IP issues? Perhaps standard-form end-user licenses or service agreements need to be reviewed to ensure that the treatment of IP is in alignment with the organization’s overall intellectual asset management policies.
- IP Exploitation: As mentioned above, an organization may be adept at innovating, and it may have a sophisticated process of cataloguing internal IP, and even assessing the gaps in that portfolio. IP commercialization and exploitation is the process by which an organization extracts value from its intellectual assets. This can be from product sales, or from out-licensing of IP-protected services and processes, as well as licensing relationships and franchise agreements, joint ventures and cross-licensing. An organization must understand the steps to market, whether through its own sales channels, or through distributorships or resellers. And the process of bringing innovations to market will be supported by a well-designed intellectual asset management system.
Richard Stobbe is an IP lawyer, trademark agent and Certified Licensing Professional. To discuss the importance of intellectual assets within your organization, contact Richard Stobbe in our Intellectual Property and Technology Group.
No commentsUpdate on Injunction Against Google (Equustek Solutions Inc. v. Google Inc.)
–
By Richard Stobbe
Last summer, Google was ordered by a Canadian court to de-index certain offending websites which were selling goods that were the subject of an intellectual property (IP) infringement claim (Equustek Solutions Inc. v. Jack, 2014 BCSC 1063 (CanLII), see our earlier post: Court Orders Google to Remove Site from Worldwide Search Results).
The underlying dispute involved a trade-secret misappropriation and passing-off claim by a manufacturer against a rival company. Google appealed the lower court decision. In Equustek Solutions Inc. v. Google Inc., 2014 BCCA 295 (CanLII), the BC Court of Appeal has rendered a decision.
Google applied for a stay of the original injunction on a number of grounds, including the argument that the original order was “unprecedented in Canadian law”, the order was “overly broad”, and that the order will have a “direct and irreversible impact†on Google. Google argued that it would suffer “irreparable harm” for two reasons: first, Google customers would be impacted, although it was not clear how exactly; and second, Google argued that this Canadian court order would open the floodgates to other similar orders against Google in other jurisdictions.
The appeal court acknowleged the importance of the case, musing that “the order of the court below raises profound issues as to the competence of Canadian courts to issue global injunctions that affect what content users around the world can access on the Internet.”
However, after balancing the arguments, the Court of Appeal did not grant the stay, so the injunction remains in place.
There are a few interesting points about this decision:
- Although Google was not a party to the original lawsuit (remember, it was an IPÂ dispute between two rival manufacturers) and no-one claimed anything against Google itself, Google took the extraordinary step of undertaking to pay damages to Equustek, for damage it might suffer if the injunction was lifted. Google said it would track traffic to the offending websites (which it is supposed to de-index) and disclose that information to Equustek. If Equustek lost profits as result of traffic to these sites, then Google would make good the damages.
- Equustek counter-argued that this was cold comfort, asking: “What value is it to have the right to sue Google for damages?â€Â If access to the offending websites was not blocked by Google, said Equustek, then Equustek would still face the burden of proving damages, and then suing Google for those damages, and in the meantime its intellectual property would continue to be devalued.
The appeal will go ahead, and while the appeal is underway, the order against Google will remain. This is one to watch.
Calgary – 07:00 MST
Court Orders Google to Remove Site from Worldwide Search Results
–
In a recent decision by the British Columbia courts (Equustek Solutions Inc. v Jack , 2014 BCSC 1063), Google has been ordered to de-index a website selling goods that were the subject of intellectual property (IP) infringement claims. While this may seem quotidian – after all, Google does comply with de-indexing requests on a regular and voluntary basis – this decision has broader implications for several reasons. This decision is the first Canadian decision to compel Google to delist a website after the so-called “right to be forgotten†case in the EU, and while that case involved personal privacy rights rather than IP rights, both cases have far-reaching implications for Google’s role in providing a practical remedy for an aggrieved party. This is a role that Google has resisted, but cannot avoid in light of its ever-expanding presence in the lives of individuals and the affairs of business.
The underlying dispute involved a trade-secret misappropriation and passing-off claim by a manufacturer against a rival company. Specifically, the plaintiff Equustek alleged that a competing product known as GW1000 was an unauthorized knock-off, built using trade secrets of the plaintiff. The plaintiff Equustek won an initial order barring sales of the offending GW1000 product and then engaged in a time-consuming process of chasing the defendant to obtain some meaningful and practical remedy. This involved repeated requests to Google to block hundreds of specific individual webpages and URLs from Google Canada search results, a game that the court described as “whac-a-moleâ€. Finally the plaintiff sought an order compelling Google to de-index the defendant’s sites from all Google search results worldwide. The resulting order is important for a number of reasons:
- In order to make its order, the court had to assert jurisdiction over Google Inc. rather than the Canadian subsidiary Google Canada. In coming to this decision, the B.C. court relied in part on the EU “right to be forgotten†case. Interestingly, the court commented that the California choice-of-law clauses in Google’s various user agreements and advertising contracts did not prevent the Canadian court from asserting jurisdiction. This is due to the fact that this dispute did not arise out of any contract-related claims. Rather, the court found that it had scope to make an order (with extra-territorial reach) over Google (a non-party) under its inherent jurisdiction under the Law and Equity Act.
- The court also commented on the fact that Google is not merely a passive site, but rather it conduct active and ongoing business with British Columbia companies and individuals.
- The court found that blocking individual URLs was not as effective as blocking so-called “mother sitesâ€. In effect, the court agreed that Google’s current practice of voluntarily complying with individual requests to block specific URLs does not provide an effective remedy. This will certainly be cited in future website blocking cases.
- Regarding Google’s role, the court commented that “Google is an innocent bystander but it is unwittingly facilitating the defendants’ ongoing breaches of this Court’s orders. There is no other practical way for the defendants’ website sales to be stopped.â€
After renewing the traditional criteria for assessing the merits of an injunction application, the court granted the order. Google is appealing this decision.
Calgary – 07:00 MST
No commentsIntellectual Asset Management Best Practices – Part 1
–
Does your organization have “intellectual assetsâ€? Regardless of what your organization does – whether it is a service-based business, or in the manufacturing sector, whether it is driven by cloud-based software or bricks-and-mortar locations, whether it is a multinational or a local start-up – chances are good that you can start to list the intellectual capital that has value in your organization. What do we mean by “intellectual assetsâ€? There are many definitions, but one broad definition is simply “knowledge that has value in your organizationâ€, and it can encompass:
- Human know-how and intellectual capital – the unwritten expertise, experience, concepts and technical knowledge that employees have in their heads; and
- Intellectual assets, including registered and unregistered intellectual property (IP) – this includes the codified or “captured†knowledge that adds to your organization’s value, such as trade secrets that might be captured in internal processes, manuals, design specifications, software source-code and other unpublished know-how, as well as the value represented by:
- Patents (including Canadian and international applications and issued patents);
- Copyright-protected works (including published and unpublished written works);
- Trademarks (including logo designs, registered and common law marks);
- Industrial designs, and other forms of registered intellectual property.
Some organizations are better at managing and obtaining value from their intellectual assets. What are the best practices for the management of these assets? In this series, we’ll review current best practices for management of intellectual assets as a competitive tool. Experts in the area of intellectual asset management have identified several layers or tiers of sophistication in the handling of such assets. Therefore, while a start-up inventor may certainly learn from the approach of Apple, Inc., each organization must look at best practices from the perspective of their organization, their resources and their stage of development. As a starting point, the following three steps lay the groundwork for future steps of IP management and value creation:
1: Conduct an Audit
The first step in any organization that is new to intellectual asset management is to conduct a review of existing assets. This is also a great exercise for organizations whose IP portfolio may be evolving – perhaps through recent growth, acquisitions, internal research and development (R&D) or divestiture. This step seeks answers to issues such as:
- What does the organization own, and what is merely licensed? What are the gaps in intellectual assets?
- Review unpatented inventions, patent applications, issued patents.
- Review software developed by or for the organization.
- Identify trade-secrets, focusing on non-public information that adds specific value to the organization, including intangibles such as customer lists, processes, early-stage prototypes, and strategic plans.
- What non-disclosure agreements or confidentiality obligations has the organization agreed to?
- Is the organization party to any IP licenses (in- or out-licenses)? Are there any co-development or joint venture agreements that involve IP creation?
- Identify the organization’s trademarks, logos and brands. Note registered and unregistered marks in use by the organization in different jurisdictions.
This audit or portfolio review process may start as a simple list, and may evolve into a more detailed table or spreadsheet. It may involve more sophisticated tracking systems which are maintained with IP counsel, to track patent maintenance fees and deadlines.
2: IP Education
An organization must also educate its personnel on the strategic importance of intellectual property within the organization.
This is a process of raising awareness and providing education about the different types of intellectual property and the organization’s policies related to these assets. This must involve the leadership of the organization and it may even trickle down to “front line†personnel. It should involve the integration of intellectual property strategy into overall business strategy, or if that IP strategy is already in place, it may involve internal education sessions and policies, such as confidentiality and invention disclosure policies. In some cases, it involves a process of educating professional advisors about the strategic role of IP in the organization.
IP counsel can play an important role to provide education, and to be a resource for developing internal policies, reviewing agreements, and drafting contractual provisions.
3: Implementing “Make versus Buy†Decisions
The next step can certainly happen in tandem with the other steps of IP portfolio analysis, and IP education. Many organizations are continuously innovating in their industry as they seek to gain and maintain their competitive advantage. However, not all organizations have the capacity to innovate internally. A medium-sized company may not have the R&D strength of its competitor, but it may still use strategic decisions to leverage the value of intellectual assets and gain an edge over competitors. Ultimately, the decisions on how to innovate involve a “make versus buy†decision. Through a screening process, an organization can weigh the various factors that influence its decision to pursue an innovation opportunity. At this stage, the organization is looking at factors such as:
- Are ideas and inventions emanating from within the organization? This is certainly enhanced when the IP education and awareness is part of the organization’s culture.
- What is the value of these ideas and inventions, as against the cost of developing the idea to a commercial product?
- Is this a core or non-core function for this organization?
- Is it more cost-effective for the organization to internally develop this as a product or innovation, to pay someone else to develop it, or to license it in from another company?
- If it is internally developed, is IP protection available, and what type of protection will it be? Is it eligible for patent protection?
Here is one example of how these different pieces may fit together:
Let’s say an organization has reviewed and listed its trade secrets during an intellectual asset audit. In the course of this process, it learned that trade secrets formed an important part of the organization’s competitive advantage, but there was a lack of any internal confidentiality policies, nor was there any invention or idea disclosure process. With the help of counsel, it developed an internal confidentiality policy, as well as a modest reward system for idea disclosures. The CEO directed IP counsel to provide a lunch-and-learn session for employees, including those in the sales team. Employees were educated about their role in the organization’s value-chain, and the importance of maintaining secrecy over confidential information and innovative ideas. After the education sessions, someone in sales came forward to describe an idea for product improvement based on recent feedback from customers. This idea was filtered through the company’s “make versus buy†decision process, leading to a product improvement which was determined to be patentable. This patentable improvement blocked competitors from adopting this product change. The company’s confidentiality policy emphasized the importance of maintaining secrecy over the improvement until the patent application was filed and the product improvement was released for sale.
To discuss the importance of intellectual assets within your organization, contact Richard Stobbe in our Intellectual Property and Technology Group.
Calgary – 07:00 MST
No commentsInternational Breach of Copyright
–
Copyright in Canada is a function of the Copyright Act – without that law, there would be no copyright. How does Canadian copyright law interact with the copyright law in other countries?
In Active Operations Management (AOM) NA Inc. et al v. Reveal Group, 2013 ONSC 8014 (CanLII) (a law-school-exam-question of a case if ever there was one), the court dealt with a claim by an Ontario company of infringement within Canada of UK copyright, by another Ontario company controlled by an Australian resident, Mr. Crouch.
The claim by AOM reads like a software vendor’s nightmare. AOM is the Canadian distributor of certain software developed in the UK. According to the allegations by AOM, Mr. Crouch copied elements of the software and a business method when he worked for an Australian licensee of the UK software. Mr. Crouch started a company in Canada and then allegedly used that as a vehicle to market a replica version of the UK software and the corresponding method in Canada. With this (Canadian) copied version of the (UK) software , Mr. Crouch allegedly lured customers away from AOM. AOM filed a lawsuit alleging breach of copyright, misappropriation of trade secrets, interference with contractual relations, unjust enrichment and misappropriation of goodwill.
Remember, AOM was not the owner of the (UK) copyright – it was merely a distributor. The question for the court was whether AOM could maintain a copyright infringement lawsuit in Canada. To complicate matters, the “software” and the “method” were owned by two different (UK) owners. AOM added these owners to the lawsuit, but did not make the specifics clear in their claim.
As the court put it: “Copyright is a very specific right attaching to a ‘work’… Copyright cannot attach to an idea such as a method. It can of course attach to the manuals or other material in which the method is described. Similarly with computer software, copyright can attach to source code, to a graphic user interface, to manuals and to other material as defined in the Act. Copyright cannot attach simply to what a computer program does. The plaintiff must specify what it is that is covered by copyright and what it alleges has been done that gives rise to the statutory remedies.”
The lessons for business?
- Software vendors from outside Canada should know that, by virtue of international copyright conventions and treaties, international copyright can be enforced under Canadian copyright law;
- The Canadian Copyright Act permits someone other than the copyright owner to sue for infringement of copyright – as long as that person has appropriate rights (such as a local distributor, as in this case). Here, AOM appeared to have rights to maintain the copyright infringement lawsuit, but did not specify its rights with enough clarity in the claim. Ensure that the chain-of-title is clear in the claim itself;
- Regarding the additional claims – in particular, the trade-secret misappropriation – the court had this guidance: “It would be ludicrous …to compel a plaintiff to set out a trade secret with precision in the pleading. To do so would destroy the secret itself. A trade secret is valuable precisely because it is secret. It may be that information will have to be provided at the production and discovery stage but at that point the proprietor of the secret may seek confidentiality orders and to the extent that those details must be put into evidence may seek a sealing order.”
Calgary – 07:00 MT
Deceit in a Licensing Agreement
–
Where a technology license carries with it an obligation to pay royalties based on revenues, how does the licensor determine if the revenues are accurately reported? The sales are known to the licensee, but the licensor has no way of determining what those sales are. Many license agreements impose reporting obligations on the licensee, so that monthly or quarterly sales are reported to the licensor, to enable accurate royalties to be calculated.  In the recent decision in XY, LLC v. Zhu , 2013 BCCA 352 (CanLII), the BC Court of Appeal dealt with a licensee who breached the terms of the technology license agreement, and committed the “tort of deceit” (that’s how lawyers say “they lied”).
In this case, the licensee did not only underreport or withhold information, they actively falsified records and thus substantially underpaid the royalties owed to the licensor. The tort of deceit is made up of these elements:
- a false representation or statement made by the defendant,
- the statement was knowingly false,
- the statement was made with the intention to deceive the plaintiff, and
- the statement materially induced the plaintiff to act, resulting in damage.
A damage award of over $8 million was awarded by the court, as an assessment of the amount would put the licensor in the position it would have been in, if the licensee had performed its obligations and paid the propert amount of royalties.
One interesting twist on appeal was whether the employees of the licensee should be personally liable. Employees are not generally held responsible for the wrongs committed by the employer. After reviewing the law, the Court of Appeal decided that the claims of deceit should be available against certain employees, and those employees were not shielded merely because they were employees acting in the course of their duties. Since these employees were actively devising ways to deceive the other side, they were acting outside the scope of regular duties, and the “just following orders†defence was not accepted by the court.
Calgary – 07:00 MST
No commentsSocial Media & Non-Competition Clauses
–
In our earlier post (Are Non-Competition Restrictions Enforceable?), we reviewed “restrictive covenants” -Â these are clauses under which employees are bound by restrictions such as non-competition restrictions, non-solicitation obligations, and other controls on the employee’s behaviour which bind the employee after termination.
In Eagle Professional Resources v. MacMullin, 2013 ONSC 2501, the court considered a dispute between two competitors -Â Eagle and Maplesoft.
Eagle alleged that its ex-employees took confidential information from Eagle, and began soliciting clients, employees, and contractors of Eagle to work for Maplesoft. The defendant ex-employees argued that they did not use any confidential information to solicit business. They asserted that any contact information that they used was already publicly available through LinkedIn or Facebook accounts.
When reviewing the enforceability of restrictive covenants in the employment context, the court reiterated a three-part test (when in doubt, there is always a handy three-part test ): ï‚·
- Does the employer have a proprietary interest entitled to protection? ï‚·
- Are the temporal and spatial features of the restrictive covenant too broad? (Put another way, are there reasonable limits in time and geographic space?)ï‚·
- Is the covenant unenforceable as being against competition generally, as opposed to a more limited covenant against solicitation of former clients?
The court concluded that “there is no evidence from Eagle, other than a very bald assertion, that it had any proprietary interest entitled to protection. According to the Defendants, the information that they learned at Eagle was all publicly available and obtained from such sources as social media websites.” There are a few take-aways from this decision:
- When drafting restrictive covenants in the employment context, non-solicitation and confidentiality clauses are more likely to stand up, whereas non-competition clauses are likely to be struck down as unenforceable, as in this case. Make sure to have your agreements reviewed;
- If a “confidential customer list” is virtually the same as the employee’s LinkedIn or Facebook contacts, then there will be no proprietary interest to protect, since the information will be publicly visible to anyone.
- The court will assume that the employer will lead with its strongest evidence. Compelling evidence of specific cases of solicitation or competition is critical for success in an application by the employer – as the court quipped “Lead with trump or risk losing”. In this case, the evidence was ambiguous or it fell outside the non-competition period.
Calgary – 7:00 MST
No commentsWhat Happens When a Franchise Agreement Ends, Part 1: Restrictive Covenants
–
A “Pet Valu†franchisee in Ontario claimed that sales were declining, so she terminated the Franchise Agreement. After termination of the agreement, her husband established a competing “Pet Stuff†business nearby. When a franchise location fails as it did in this case, what happens with the “restrictive covenants†in the agreement? Can these provisions be circumvented by the use of a separate company, or by using a friend or family member?
If you are in the franchise business, either as a franchisor or a franchisee, you will undoubtedly have to deal with “restrictive covenantsâ€. These are the provisions in the Franchise Agreement that control what the franchisee can do after the termination of the agreement. Most franchise agreements contain clauses prohibiting the franchisee from establishing a competing business, soliciting customers, or using confidential information of the franchise.
The recent decision in Pet Valu Canada Inc. v. 1381114 Ontario Limited, 2013 ONSC 5361, dealt with an ex-franchisee who established a competing business through her husband’s numbered company within a few blocks of an existing Pet Valu location. Pet Valu, the franchisor, applied to the court for an injunction to compel the ex-franchisee to stop this competition. Pet Value sued both the franchisee and her husband, and each of their companies. Pet Valu argued that the actions of the ex-franchisee breached the terms of the franchise agreement which prohibited:
- the operation of a competing business for a period of 2 years after the end of the franchise agreement within a 20 km radius of any other Pet Valu Store,
- the hiring of any employee of a Pet Valu franchise for 1 year after the end of the Franchise Agreement; and
- the use of customer lists, confidential information and all Pet Valu branded signs, labels and price tags after the termination of the agreement.
The court in this case had no trouble looking behind this “transparent effort†on the part of the ex-franchisee to establish a competing “Pet Stuff†business. The “Pet Stuff†business also hired away one of the store managers who had worked at the Pet Valu franchise, and even made use of shelving and inventory with distinctive labels, price tags and product codes from the old Pet Valu franchise. The court issued an interim injunction against the ex-franchisee and her husband.
Related Reading: Richard Stobbe was recently interviewed by Alberta Venture magazine for the article Is buying a franchise the opportunity of a lifetime, or the worst mistake you’ll ever make?
Calgary – 07:00 MST
No commentsKeeping Secrets: Trade Secrets and Confidentiality Agreements
–
My article on Keeping Secrets: Trade Secrets and Confidentiality Agreements is published in the latest issue of The Advisor. This article reviews confidentiality agreements and the decisions in Convolve, Inc. and Massachusetts Institute of Technology v. Compaq Computer Corporation and Seagate Technology, LLC and Plaza Consulting Inc. v. Grieve.
Calgary – 07:00 MDT
No commentsAll Tied Up: Restrictive Covenants After Sale of a Business
–
Restrictive covenants attempt to tie up a business person who sells a business, in order to restrict that person from competing against the business they just sold. In an earlier post (Are Non-Competition Restrictions Enforceable?), we reviewed restrictive covenants in the context of employment agreements. The Supreme Court of Canada recently weighed in on the topic of restrictive covenants in the context of a commercial transaction. While this is not specifically an intellectual property law topic, it is a very common issue faced by technology companies.
In Payette v. Guay Inc. , 2013 SCC 45, the court reviewed the enforceability of non-competition and non-solicitation clauses in an asset purchase and sale agreement. While there was also a restrictive covenant in place in an employment agreement, the case really turned on the enforceability of the restrictions arising from the purchase and sale agreement. The court was clear that different rules apply to each type of agreement. The court provides the following guidance for those negotiating restrictive covenants:
- “In the commercial context, a restrictive covenant is lawful unless it can be established on a balance of probabilities that its scope is unreasonable having regard to the context in which it was negotiated.”
- “A non-competition covenant will be found to be reasonable and lawful provided that it is limited, as to its term and to the territory and activities to which it applies, to whatever is necessary for the protection of the legitimate interests of the party in whose favour it was granted.” In this case, a five year period was reasonable in light of the highly specialized nature of the business.
- “While it is true that in the case of a non-competition covenant, the territory to which the covenant applies must be identified, a determination that a non-solicitation covenant is reasonable and lawful does not generally require a territorial limitation.” In this case, there was no territorial limitation in the case of the non-solicitation clause, but the clause was still upheld as reasonable.
This decision is good news for buyers who are acquiring a business and wish to impose enforceable non-competition and non-solicitation restrictions on the seller. The Supreme Court of Canada is clear that different rules apply in the employment context and anyone negotiating these agreements should take note.
Calgary – 07:00 MDT
No commentsTrade-Secrets and the Departing Employee
–
Concerned about departing employees who might have confidential information about your business and clients? Or maybe you are the ex-employee and you are unsure of where the line is drawn when departing one job to start another.
In Plaza Consulting Inc. v. Grieve et al , 2013 ONSC 5338 (CanLII), the court addressed an injunction application by QA Consultants, a Canadian company offering software testing and quality assurance services, against former employees and consultants who started a competing business. The court provides some guidance on how these matters are held, when ex-employees are accused of misappropriating confidential information and poaching customers. In this case, the court says:
- Whether dealing with employees who allegedly misappropriate their former employer’s business methods in breach of a restrictive covenant or in breach of fiduciary duties, the employer must at the very least establish that it “has a proprietary interest that is entitled to protection.†Aon Consulting Inc. v Watson Wyatt & Co., 2005 CarswellOnt 3706, at para 16 (SCJ). Here, the court concludes that the confidential information in question is “highly generic”. Remember that “[a] trade secret cannot be within the realm of general skills or knowledge.”
- AÂ party who receives allegedly confidential information and who is accused of misusing it must have done so to the detriment of the party that provided the information in the first place. International Corona Resources Ltd. v Lac Minerals Ltd. 1989 CanLII 34 (SCC), (1989), 26 CPR (3d) 97, at 103(SCC). In this case, the court found that the information in question was not used to the detriment of the plaintiff.
- In the case of the allegations of solicitation of former clients or employees of QA Consultants, the court indicated that, in these agreements, the restrictive covenants were sufficiently vague that the allegations made against the ex-employees were not “clear†breaches of those covenants. The vague definition in the agreements did not help the case. Ultimately, the injunction application was dismissed.
Remember to get advice on the restrictive covenants in employment agreements. Both employees, consultants and employers should understand the scope of confidentiality obligations and non-solicitation restrictions.
- Calgary – 07:00 MDT
Non-Disclosure Agreements: A Cautionary Tale
–
Agreements which contain non-disclosure obligations (also known as a confidentiality agreements, CAs, NDAs or confidential disclosure agreements) are common in many industries – from licensing deals to franchise agreements, from manufacturing to retail industries. Confidential information may be disclosed during early-stage negotiations, even before a formal contractual relationship is concluded. Or it may be disclosed in the course of an ongoing contract, for example, a licensing or manufacturing agreement. In all of these cases, the exact definition of “Confidential Information” may be critical.
In CONVOLVE, INC. AND MASSACHUSETTS INSTITUTE OF TECHNOLOGY v. COMPAQ COMPUTER CORPORATION and SEAGATE TECHNOLOGY, LLC, the US Federal Circuit Court of Appeals dealt with a claim for misappropriation of trade-secrets and breach of confidence, arising out of a certain Non-Disclosure Agreement (NDA) signed between the parties.
The Court noted that: “The NDA states that, to trigger either party’s obligations, the disclosed information must be: (1) marked as confidential at the time of disclosure; or (2) unmarked, but treated as confidential at the time of disclosure, and later designated confidential in a written memorandum summarizing and identifying the confidential information.” This definition of confidential information meant that certain disclosures by Convolve which failed to include a written designation or notification of confidentiality were not considered to be confidential. The failure to mark that information as “confidential” meant that the information was not caught by the agreement. The Court also decided that Convolve’s remedies under the California Uniform Trade Secrets Act (CUTSA) were pre-empted by this NDA, leaving Convolve (the disclosing party) without any remedy for misappropriation of this information by the other side.
Lessons for business?
- While this decision turns, in part, upon an interpretation of US law (remember there is no equivalent of the Uniform Trade Secrets Act in Canada), the take-away is the same: NDAs are not just “boilerplate”. They protect the secrets of your organization, the information that gives you an advantage over the competition.
- The definition of “Confidential Information” is important, and following the definition of “Confidential Information” is just as important. The first may be easy to focus on while the agreement is being negotiated and vetted by legal. The second is more difficult to remember as the parties engage in fast-paced negotiations, and information is disclosed by personnel within the organization who may never actually see the written NDA.
Calgary – 07:00 MDT
No commentsProtecting IP Rights
-Â
The protection of IP rights is a competitive tool in the global economy. A recent report from authored by Dennis Blair, former director of national intelligence in the U.S. and Jon Huntsman Jr. former governor of Utah and U.S. ambassador to China (and probably the most decent of the candidates running for the GOP last year) discuss this in their recent article in the Washington Post. They both work for the Commission on the Theft of American Intellectual Property (The IP Commission).
On Wednesday, the IP Commission released its report: The Report of the Commission on the Theft of American Intellectual Property (PDF). Makes for interesting reading for Canadians.
The Americans have the Economic Espionage Act, the Foreign Economic Espionage Penalty Enhancement Act and the Theft of Trade Secrets Clarification Act.
Is it time for Canadian legislation on the protection of trade secrets?
Calgary – 07:00 MDT
Â
No comments